Most enterprise buyers now ask for assurance artifacts before procurement. Without operational security and continuous evidence, deals stall even when teams think they are "ready" on paper. SOC 2 Vendor Risk Mapping is the discipline that turns vendor governance from a compliance task into a core part of your security program.
This article gives technology and compliance leaders a practical blueprint to create a vendor risk map that matches SOC 2, supports real-world audit needs, and makes your sales cycles smoother. You will learn the essential concepts, step‑by‑step actions, real examples, and tips for teams with limited time.
Why Vendor Risk Matters for Enterprise‑Facing Companies

1) Third parties expand the attack surface: Modern businesses run on software and managed services. SAFE Security points out that the attack surface, once protected behind firewalls, now spans hundreds or thousands of vendors performing critical functions. Each connection represents a potential path for attackers or an insider mistake. Regulators are taking notice. The U.S. Federal Reserve warned banks in 2024 that outsourcing services does not relieve them of responsibility for compliance.
2) Data breaches and costs keep rising: IBM’s 2025 Cost of a Data Breach Report found that global breach costs fell slightly to USD 4.44 million but U.S. breach costs rose to USD 10.22 million due to regulatory penalties and slower detection. Bitsight research shows that 30% of breaches involve third parties, yet only one in three enterprises continuously monitor all third‑party relationships. These numbers underline why SOC 2 Vendor Risk Mapping is not optional.
3) Enterprises demand evidence: Large buyers often require proof of vendor controls before signing contracts. Bitsight emphasises that vendor risk management must be a priority because effective practices protect sensitive data and maintain security posture. Traditional tactics, such as annual spreadsheets, can’t keep up with fast-changing risk. Vendors that can map risks to SOC 2 and demonstrate ongoing monitoring win trust and shorten sales cycles.
4) Business benefits: A structured vendor risk posture reduces operational surprises, improves audit readiness, and accelerates revenue. By showing strong mapping you reduce the chance of a vendor‑driven breach, avoid regulatory sanctions, and reassure buyers that your controls extend to your suppliers. For example, Konfirmity’s managed service helps clients achieve SOC 2 readiness in 4‑5 months with about 75 hours of internal effort per year, compared to 550–600 hours on their own. An efficient process saves not just time but confidence when negotiating enterprise agreements.
CTA: Book a demo
What Is SOC 2 and Why It Matters for Vendor Risk
The American Institute of Certified Public Accountants (AICPA) defines SOC 2 as a report on controls at a service organization relevant to security, availability, processing integrity, confidentiality, or privacy. These reports are intended to meet the needs of users who need detailed information and assurance about those controls. A SOC 2 Type I report evaluates the design of controls at a point in time, while a Type II report examines the operating effectiveness over a period of six to twelve months. Vendor management is part of the SOC 2 environment because suppliers often process or store customer data. Auditors examine how you identify, assess, and monitor these third‑party risks.
The five Trust Services Criteria: Security focuses on protecting information from unauthorised access; Availability ensures systems remain reliable for employees and clients; Processing Integrity verifies that systems operate as intended; Confidentiality deals with limiting access, storage, and use of confidential information; and Privacy covers safeguarding personally identifiable information. Security is mandatory in every SOC 2 report; the other criteria can be scoped based on services. Understanding these criteria is essential when mapping vendor risks because each vendor function may touch different criteria.

Why does SOC 2 Vendor Risk Mapping matter?
A SOC 2 report helps you evaluate how well a company identifies, assesses, mitigates, and monitors risks—including those posed by vendors. Proper vendor management mitigates the severity and frequency of data breaches and protects business continuity. SAFE Security explains that vendor risk management assesses risks from both directions: the risk a vendor poses to you and the risk they face themselves. By mapping vendor risks to SOC 2 controls, you can show auditors and buyers that your entire control environment, including third parties, meets the Trust Services Criteria.
What Vendor Risk Mapping Means in Practice
SOC 2 Vendor Risk Mapping means going further than superficial questionnaires. It involves identifying each vendor, analysing how they interact with your systems and data, linking those exposures to your internal controls, and ensuring mitigation and monitoring. The goal is to integrate vendor governance into your daily security program so you can produce evidence during audits and reassure customers.
Essential components include:
- Vendor assessment: Build a full inventory of vendors and understand what data or systems they touch.
- Risk analysis: Classify vendors by risk and criticality based on access to data, regulatory obligations, and business impact.
- Security controls: Map vendor exposures to specific SOC 2 control domains and define measures to mitigate them.
- Due diligence: Collect SOC 2 reports, ISO 27001 certificates, or questionnaires as evidence.
- Process mapping: Integrate vendor lifecycle processes—onboarding, monitoring, off‑boarding—with your internal control framework.
- Vendor governance: Integrate risk mapping into procurement and legal workflows, ensuring contracts include control expectations and right‑to‑audit clauses.
- Audit readiness: Maintain documentation, evidence, and reporting so you can demonstrate consistent monitoring when auditors or customers ask.
For busy teams, the challenge is scale. Bitsight research shows that large enterprises manage tens of thousands of third parties, while SAFE Security warns that outdated methods persist because they have become standard practice. That’s why efficient templates, tiering logic, and automation are vital. Konfirmity’s managed service reduces internal effort to about 75 hours annually by using pre‑populated questionnaires, risk‑tiering rules, and dashboards.
CTA: Book a demo
Step‑by‑Step Guide to SOC 2 Vendor Risk Mapping
This section outlines eight actionable steps for SOC 2 Vendor Risk Mapping. Each step includes guidance, examples, and tips for busy teams.
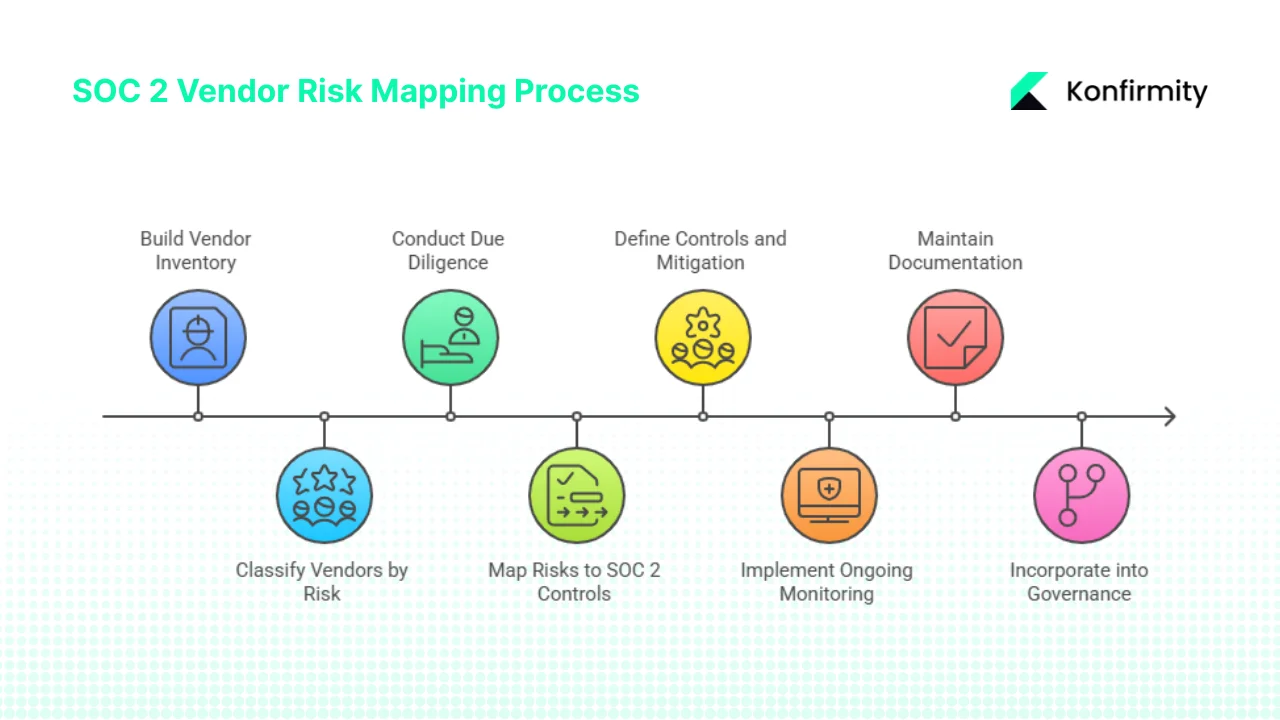
Step 1: Build Your Vendor Inventory
Identify every third party that touches your customer data, processing systems, infrastructure, or corporate functions. Vendors include cloud service providers, data centres, payment processors, help‑desk tools, contractors, and even external developers. SAFE Security emphasises that the vendor risk management lifecycle starts with selection and onboarding and continues through off‑boarding. Use automation to scan your environment—your identity provider and finance systems can reveal hidden suppliers. Example: a SaaS company might list AWS (infrastructure), Stripe (payment processing), Zendesk (support), Okta (identity), and Jira (development workflow).
Step 2: Classify and Tier Vendors by Risk
Determine each vendor’s criticality based on the sensitivity of data and the impact of service disruption. A three‑tier model works well: Tier 1 (critical) vendors directly impact your product or host confidential data; Tier 2 vendors provide important support services; Tier 3 vendors have limited access or non‑critical functions. Bitsight’s research shows that only 17% of organisations can inventory a majority of their assets, so thorough discovery is essential. Assign higher monitoring frequency and more rigorous controls to Tier 1 vendors. Link this process to your procurement workflow so classification happens before signing contracts.
Step 3: Conduct Due Diligence and Vendor Assessments
Collect evidence from each vendor at onboarding and periodically thereafter. Evidence includes SOC 2 Type II reports (if available), ISO 27001 or PCI DSS certificates, security questionnaires aligned to SOC 2 criteria, penetration test summaries, and incident history. Bitsight stresses that traditional VRM tactics aren’t enough; evidence must be current and meaningful. A tier‑based approach can prioritise deeper assessments for high‑risk vendors. For example, Tier 1 vendors should provide a recent SOC 2 report and complete a detailed questionnaire addressing encryption, access controls, incident response, and disaster recovery. Tier 3 vendors may only need a short questionnaire and self‑attestation. Record all evidence in a central repository.
Step 4: Map Vendor Risks to Your SOC 2 Control Framework
For each vendor, identify what trust criteria are relevant. A cloud storage provider handling customer files maps to Security and Confidentiality; a payroll service might map to Privacy and Processing Integrity; a help‑desk tool might relate to Availability and Security. Use your internal control set (e.g., access reviews, change management, encryption, monitoring) and connect vendor exposures to those controls. Create a matrix linking vendor risks to controls. This mapping not only clarifies responsibilities but also supports evidence collection. Example: Vendor A processes confidential financial data; map to Confidentiality and Security; internal control requirement: data encrypted at rest and regular access reviews.
Step 5: Define Controls and Mitigation for Each Vendor Risk
Identify whether the vendor already has controls that meet your expectations or if you need compensating actions. Compensating measures can include contractual clauses requiring specific security practices, service agreements (SLAs) around uptime and incident reporting, monitoring by your security team, or additional technical controls such as proxy filtering or endpoint detection. SAFE Security lists top vendor controls such as email security, endpoint detection, multi‑factor authentication, secure software, incident response, and data encryption. Make sure each risk has an associated control and evidence requirement. For example, if a vendor lacks a SOC 2 report, you might require them to enable logging and provide monthly security metrics.
Step 6: Implement Ongoing Monitoring and Review
Vendor risk mapping is not a one‑off event. Set a review cadence based on vendor tier. High‑risk vendors should be reviewed at least quarterly with updated reports, security ratings, and incident checks. Lower‑tier vendors may be reviewed annually. Bitsight research shows that static frameworks quickly become obsolete because threats and vendor environments change. Use automation to monitor vendor security performance, news about breaches, regulatory changes, and contract expirations. Integrate findings into your risk register and update controls accordingly.
Step 7: Maintain Documentation, Audit Evidence, and Reporting
Track all vendor assessments, risk mappings, control definitions, and review outcomes in a central system. Auditors and enterprise customers will ask for evidence that you identify, assess, and monitor vendors. Maintain copies of SOC 2 reports, questionnaires, risk ratings, and remediation actions. Provide dashboards that summarise how many vendors are in each tier, which trust criteria they map to, and their compliance status. This ensures audit readiness and internal accountability.
Step 8: Incorporate Vendor Risk Mapping into Governance and Procurement
Embed the entire process into your procurement, legal, and vendor onboarding workflows. Ensure contracts include security requirements, right‑to‑audit clauses, and remediation timelines. Link vendor risk mapping with your broader risk management program, compliance auditing schedule, and business continuity plans. Plan for off‑boarding: when terminating a vendor, cancel access, verify deletion of data, and follow up for any residual issues.
Real‑World Examples
To illustrate SOC 2 Vendor Risk Mapping in practice, here are two hypothetical scenarios of a SaaS provider selling to large enterprise customers. These examples show how an inventory flows into tiering, assessment, mapping, controls, and monitoring.
These simple cases show clearly how different vendors map to different trust criteria and require different degrees of oversight.
Templates and Tools for Busy Teams
Vendor Risk Mapping Template.
Create a structured template to capture information for each vendor. A basic layout should include: vendor name; tier/criticality; data or systems accessed; identified exposures; SOC 2 trust criteria linked; controls in place (both vendor and internal); evidence/documents collected (audit reports, certificates, questionnaires); monitoring cadence; and responsible owner. Pre‑populate sections for common vendors to save time.
Assessment Questionnaire Sample.
Build a questionnaire aligned with the five trust criteria. Examples: “Do you encrypt data in transit and at rest?” (Security and Confidentiality), “Do you have redundant systems and disaster recovery plans?” (Availability), “How do you ensure processing accuracy and integrity?” (Processing Integrity), “Who has access to confidential data and how do you enforce least privilege?” (Confidentiality and Privacy), and “Can you provide a SOC 2 Type II report covering your systems?” (Evidence). Bitsight notes that questionnaires alone are insufficient, so combine them with evidence from SOC 2 reports or scans.
Process Workflow Diagram.
A simple flow helps stakeholders grasp the process: Onboard vendor → Tier vendor → Assess vendor → Map risks to SOC 2 → Define controls → Implement monitoring and review → Report to stakeholders → Off‑board when necessary. Keep the diagram in your documentation or GRC tool so teams follow the same path every time.
Dashboard and Metric Suggestions.
Track metrics that matter: number of critical vendors reviewed in the current quarter; percentage of vendors with current SOC 2 reports; number of vendor incidents or findings; percentage of vendors mapped to each trust criterion; average time to resolve vendor findings; and compliance status across frameworks. Visual dashboards help leadership understand progress and allocate resources.
Automation and Tools.
When considering a vendor risk management solution, explore options like a dedicated platform or a managed service such as Konfirmity. Konfirmity not only provides an in-depth product but also offers hands-on managed services. Our team's extensive experience, which includes over 6,000 completed audits and 25 combined years in the field, helps clients. By using Konfirmity, organizations can significantly cut internal effort from an estimated 550–600 hours annually to approximately 75 hours, while also accelerating SOC 2 readiness to just 4–5 months. Key features to seek in any platform evaluation include integration with identity providers, risk scoring based on CVSS, and the ability to provide real-time alerts.
CTA: Book a demo
Common Pitfalls and Best Practices
Pitfalls to avoid:
- Treating vendor risk as a one‑time event. One‑off assessments miss continuous changes in vendor environments and evolving threats. Bitsight warns that static frameworks become obsolete minutes after approval.
- Focusing only on certificates. A SOC 2 report is valuable, but relying solely on a certificate without mapping to your controls leaves blind spots. Vendors can have certified systems but still introduce unmitigated risks.
- Manual, spreadsheet‑driven workflows. Manual tracking becomes unmanageable as vendors scale and can lead to stale data. SAFE Security notes that existing methods are outdated and inaccurate.
- Ignoring lower‑tier vendors. Even seemingly minor suppliers can become entry points if they connect to your network or have fourth‑party dependencies.
- Neglecting off‑boarding. If you fail to revoke access and verify data deletion, residual risks remain.
Best practices to adopt:
- Maintain a changing inventory and tiering logic that adapts as your vendor list grows or services change.
- Link vendor risk mapping with your overall risk management and SOC 2 program. Map each vendor exposure to specific controls and trust criteria.
- Keep documentation and evidence ready. Auditors want to see proof that you assessed vendors, mapped risks, and applied controls.
- Use automation and managed services where possible. Offload questionnaire distribution, evidence collection, and monitoring to tools or partners. Konfirmity’s “human‑led, managed security and compliance” model emphasises execution rather than advice.
- Review vendor risk mapping regularly and adjust when services, scope, or regulatory requirements change.
- Involve cross‑functional teams—security, procurement, legal, and business—to ensure that vendor risk considerations are integrated into contracts and operations.
- Communicate your vendor risk posture. Provide dashboards or reports to enterprise customers to build trust. Your ability to show continuous governance can set you apart in competitive sales processes.
CTA: Book a demo
Conclusion
SOC 2 Vendor Risk Mapping is more than a compliance checklist. It is a structured, evidence‑driven method to manage third‑party exposures, meet audit requirements, and support enterprise deals. The process starts with a full vendor inventory, continues through risk tiering, due diligence, mapping risks to trust criteria, defining controls, monitoring, documentation, and integration into procurement. By following the practical steps outlined above, you can build a vendor governance program that stands up to buyers, auditors, and attackers.
Real security demands year‑round attention. Konfirmity’s experience—over 6,000 audits and 25 years in the field—shows that with the right mix of automation and human expertise you can achieve SOC 2 readiness in 4–5 months while cutting your internal effort dramatically. In a world where attackers exploit every link in the supply chain and regulators hold organisations accountable for vendor failings, investing in SOC 2 Vendor Risk Mapping pays dividends. Start with security and arrive at compliance. Design a program that operates every day, not just before the audit, and you will gain the trust of enterprise clients and the resilience to keep your business running.
FAQs
Q1. What is SOC in vendor management?
SOC stands for Service Organization Controls. SOC 2 focuses on controls relevant to security, availability, processing integrity, confidentiality, and privacy. In vendor management, it means evaluating third‑party vendors to ensure their controls meet the SOC 2 Trust Services Criteria and that they have processes for identifying, assessing, mitigating, and monitoring risks.
Q2. What are the 5 criteria for SOC 2?
The five Trust Services Criteria are Security, Availability, Processing Integrity, Confidentiality, and Privacy. Security is mandatory for every SOC 2 audit, while the other criteria are scoped based on services.
Q3. What is the SOC 2 risk management framework?
SOC 2 does not prescribe a named risk management framework, but auditors require organisations to identify and assess risks—including vendor risks—implement controls mapped to those risks, monitor those controls over time, and provide evidence that they operate effectively. The SOC 2 Vendor Risk Mapping process described above is an example of applying risk identification, control mapping, monitoring, and evidence collection within the context of SOC 2 and third‑party management.
Q4. How do you perform a vendor risk assessment?
A concise process is: (1) build a vendor inventory; (2) classify and tier vendors by criticality and exposure; (3) collect documentation and conduct due diligence; (4) identify vendor risks (data access, system access, regulatory obligations, incident history); (5) map those risks to your controls and relevant SOC 2 criteria; (6) define mitigation and monitoring measures; (7) implement a review cadence and monitor vendor performance and incidents; and (8) document everything for audit readiness. These steps connect with best practices from authoritative sources such as Bitsight, Censinet, and Secureframe.





.svg)





.svg)
.svg)