Most enterprise buyers now request assurance artefacts before procurement. Deals stall when teams think they are ready on paper yet cannot prove that controls are working. Meanwhile, the global average cost of a data breach was about USD 4.44 million in early 2025, while fines under the EU General Data Protection Regulation (GDPR) have totalled more than €5.65 billion since 2018. Auditors and data protection authorities are intensifying scrutiny across industries, and enterprise clients are asking suppliers to demonstrate operational security rather than tick‑box compliance. In this guide, written from the perspective of Amit Gupta of Konfirmity, we explain why GDPR Audit Preparation is essential for companies selling to enterprise clients, highlight common pitfalls, outline a step‑by‑step audit process, provide practical templates, and show how audit readiness pays off.
Why GDPR Audit Preparation Matters for Enterprise‑Selling Firms
Enforcement and market pressure
The enforcement climate is unforgiving. The CMS enforcement tracker notes that by early 2025 the cumulative sum of fines under the GDPR exceeded €5.65 billion and that the average fine across 2018–2025 was more than €2.36 million. The top fines include a €1.2 billion penalty against a technology firm for unlawful data transfers and several hundreds‑of‑millions fines against social media and e‑commerce platforms. Regulators are also targeting other industries; by January 2025 the total of all GDPR fines reached about €5.88 billion and enforcement had expanded into finance, healthcare and energy. When investigations discover incomplete records, inadequate legal bases or weak technical controls, enterprise clients lose trust and vendors lose deals.
Outside Europe, data‑breach costs continue to rise. IBM’s Cost of a Data Breach 2025 report shows that the global average breach cost fell slightly to about USD 4.44 million due to quicker containment, yet in the United States the average breach cost surged past USD 10 million. Morgan Lewis notes that the 2024 average breach cost climbed to $4.88 million, with healthcare breaches in the United States averaging $9.77 million. Longer breach lifecycles (>200 days) cost organisations around $5.46 million. This combination of regulatory penalties and breach costs means enterprise buyers insist on evidence that suppliers protect personal data.
Beyond checklists
Treating GDPR compliance as a checklist can backfire. Filling in policies and copying boilerplate templates may appear sufficient, but auditors and clients will test whether controls operate effectively. Missing consent logs, outdated processing inventories or undocumented data flows are obvious red flags. Konfirmity’s team has supported more than 6,000 audits over 25 years; in our experience, companies that approach compliance as a one‑off project often scramble during audits and struggle to answer due‑diligence questionnaires. Conversely, teams that implement continuous evidence collection reduce audit preparation time by roughly 75%, achieving SOC 2 readiness in four to five months instead of nine to twelve months, and spending around 75 hours per year on evidence tasks compared with 550–600 hours for self‑managed programmes. Enterprise customers reward this level of preparation with faster procurement cycles and deeper trust.
What Is a GDPR Audit — Scope, Purpose and Applicability
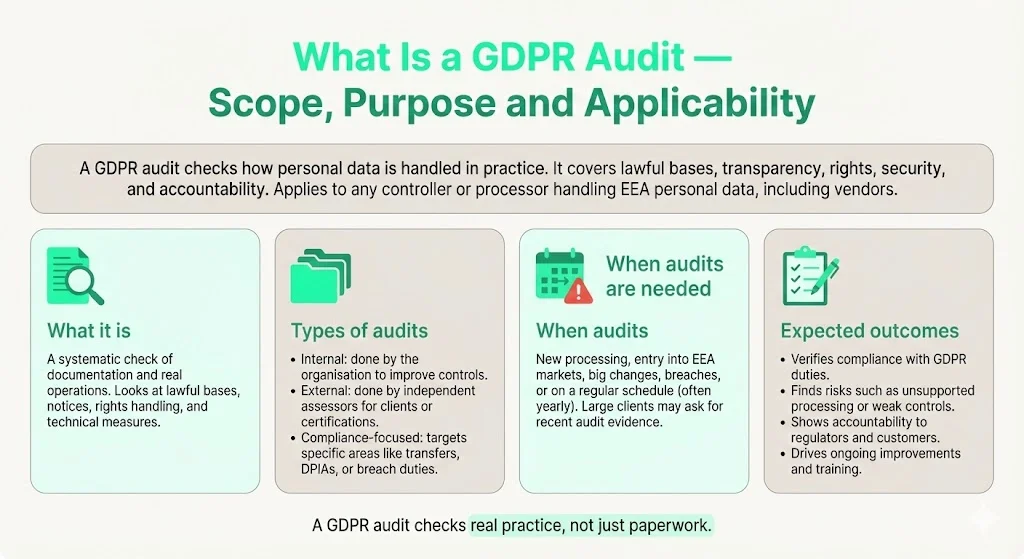
A GDPR audit is a systematic assessment of how an organisation processes personal data relative to the requirements of the GDPR. Unlike a simple gap analysis, a GDPR audit reviews both documentation and operational practices to confirm that lawful bases, transparency obligations, data‑subject rights, security controls and accountability measures are consistently implemented. It applies to any controller or processor that handles personal data of individuals in the European Economic Area (EEA), irrespective of the organisation’s location, and it can extend to vendors or subprocessors that support those activities.
Types of audits
- Internal audit – performed by an organisation’s own audit or risk team to verify compliance and improve processes. For example, ISO 27001 clause 9.2 requires organisations to conduct internal audits at planned intervals.
- External audit – conducted by an independent assessor to provide assurance to customers or regulators. Enterprise clients may require external audits for certifications (e.g., ISO 27001 Stage 2) or due‑diligence. For SOC 2 Type II, an external auditor reviews evidence over an observation period of three to twelve months.
- Compliance audit – focuses on specific obligations such as cross‑border data transfers, data‑protection impact assessments (DPIAs) or breach notification procedures. Regulators may initiate a compliance audit after a breach or as part of enforcement investigations.
When audits are needed
A GDPR audit should be initiated whenever an organisation introduces new data processing activities, expands into EEA markets, undergoes major organisational changes (such as mergers or new product launches), experiences a data breach, or at regular intervals (often annually) to maintain compliance. Enterprise buyers may require suppliers to produce a recent audit report as part of procurement due‑diligence.
Expected outcomes
A well‑executed GDPR audit:
- Verifies compliance – ensures that lawful bases, transparency obligations, data‑subject rights and security controls meet the regulation.
- Identifies risks – uncovers hidden data flows, unsupported processing purposes or inadequate technical measures that could lead to fines or breaches.
- Demonstrates accountability – provides evidence to regulators and clients that the organisation knows how it processes data and can prove itdataprotection.ie.
- Promotes continuous improvement – triggers corrective actions, process enhancements and training to embed data protection into everyday operations.
Core GDPR Principles and Compliance Pillars
Article 5 of the GDPR sets out the fundamental principles of data protection. They underpin every audit and should guide the design of controls.
Key principles
- Lawfulness, fairness and transparency – personal data must be processed lawfully, fairly and in a transparent manner.
- Purpose limitation – data must be collected for specified, explicit and legitimate purposes and not further processed in a way incompatible with those purposes.
- Data minimisation – collect only the data that is necessary for the stated purpose.
- Accuracy – ensure personal data is accurate and kept up to date; inaccurate data should be erased or rectified without delay.
- Storage limitation – keep data in a form that permits identification of data subjects for no longer than necessary.
- Integrity and confidentiality – process data in a manner that ensures appropriate security, including protection against unauthorised or unlawful processing and against accidental loss.
Turning principles into compliance pillars
To operationalise these principles, organisations should focus on six pillars:
- Lawful basis for processing – document the legal grounds (e.g., consent, contract, legitimate interest) for each processing activity. Article 30 requires controllers to maintain a Record of Processing Activities (RoPA) and provide it to the Data Protection Commission on requestdataprotection.ie.
- Transparent privacy and consent policies – publish clear notices that describe the purpose of processing, retention periods and data‑subject rights. Keep consent workflows (cookie banners, marketing opt‑ins) consistent and demonstrable.
- Data‑subject rights – implement procedures to handle access, rectification, deletion, restriction, objection and portability requests within statutory timeframes.
- Security of processing – apply technical measures such as encryption, access controls, pseudonymisation, logging and monitoring. Controls should align with recognised frameworks like ISO 27001 (Annex A controls), SOC 2 Trust Services Criteria and NIST guidelines.
- Accountability and documentation – maintain RoPA, consent logs, DPIA reports, incident response records and policy version histories. Auditors and clients will ask for evidence of decisions and actions.
- Vendor and third‑party compliance – ensure processors sign data‑processing agreements (DPAs), implement appropriate safeguards and allow audits. Review their certifications (ISO 27001, SOC 2) and security posture regularly.
Adhering to these pillars does more than satisfy regulators. For enterprise clients, a mature privacy programme signals that a vendor can be trusted with sensitive data. It reduces the buyer’s risk and accelerates procurement.
Pre‑Audit: Preparing Your Organisation (Readiness Phase)
A successful GDPR audit begins with thorough preparation. Busy teams often underestimate the effort required to map data flows, update policies and train personnel. The readiness phase should be treated as an operational project, not a paperwork exercise.
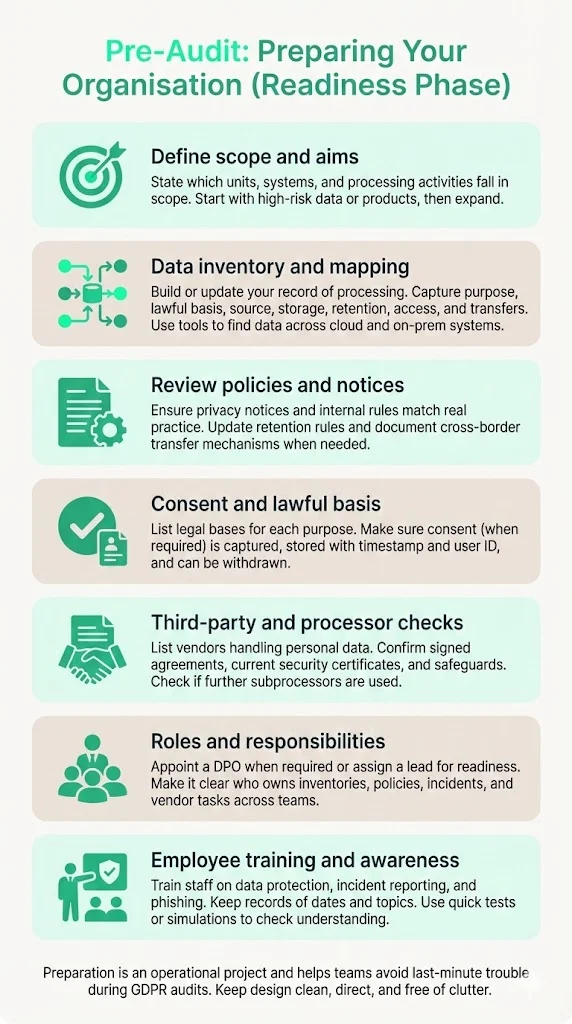
- Define scope and objectives – agree on which business units, systems and processing activities will be audited. In early stages, it may be sensible to focus on specific products or high‑risk data (e.g., marketing database, customer analytics) before expanding to the entire organisation.
- Conduct data inventory and mapping – build or update your RoPA. Capture for each data category: purpose, lawful basis, source, storage location, retention period, access controls and third‑party transfers. The Irish Data Protection Commission stresses that an accurate RoPA demonstrates awareness of all processing activities and supports accountabilitydataprotection.ie. Use data‑discovery tools to locate structured and unstructured data across clouds and on‑premises systems.
- Review and update privacy and data‑protection policies – ensure public privacy notices, internal data‑protection policies and procedural documents reflect actual practices. Align retention rules with purpose limitation and storage limitation principles. Document cross‑border transfer mechanisms (e.g., standard contractual clauses) where applicable.
- Consent management and lawful basis mapping – catalogue the legal bases used for each processing purpose, and verify that consent is collected, documented and revocable for activities requiring it (marketing emails, targeted advertising, cookies). Implement tooling to record consent timestamp, user identifier, consent status and withdrawal status.
- Third‑party vendor and processor review – compile a list of all vendors and subprocessors who handle personal data. For each vendor, confirm there is a signed DPA, that security certifications are current, and that data‑transfer safeguards are appropriate. Assess whether the vendor allows audits and whether they use additional subprocessors.
- Assign roles and responsibilities – designate a Data Protection Officer (DPO) if required, or appoint a compliance lead to coordinate audit readiness. Clarify ownership of data inventories, policies, incident response and vendor management across legal, IT, product and HR teams.
- Employee training and awareness – provide training on data‑protection principles, handling of personal data, incident reporting and phishing awareness. Maintain records of who was trained, when, and on what topics. Test understanding through spot‑checks or simulations.
Audit Execution: Step‑By‑Step Process
Once the groundwork is complete, the audit itself follows a structured path. At Konfirmity we break this down into clear stages and accompany clients through each one. The diagram below visualises the flow from readiness to execution and continuous compliance.
Step 1: Planning and scoping
Define the audit scope in detail, covering systems, data categories, geographies and third parties. Agree on objectives and deliverables with the auditor. Set a realistic timeline and allocate internal resources. For SOC 2 Type II and ISO 27001, the observation period may span three to twelve months; plan accordingly to provide sufficient evidence.
Step 2: Data mapping and inventory review
Revisit the RoPA and validate that all data flows identified during the readiness phase are accurate. Verify that categories, processing purposes, retention schedules and transfer mechanisms are documented. Confirm that deletion processes exist for expired data. This step often uncovers shadow systems or manual processes that were missed during preparation.
Step 3: Policy, procedure and documentation audit
Collect and present all relevant policies and procedures: privacy notices, internal data‑protection policies, consent workflows, DPIAs, security policies, incident‑response plans and vendor management procedures. Audit evidence also includes RoPA records, version histories and board approvals. Missing or outdated documentation is a common reason for audit findings.
Step 4: Technical and organisational security review
Auditors will assess the effectiveness of security controls. Expect detailed questions on:
- Encryption and key management – data at rest and in transit; encryption algorithms; key rotation practices;
- Access controls – role‑based access, multi‑factor authentication, least‑privilege enforcement, periodic access reviews;
- Pseudonymisation and anonymisation – techniques used and their effectiveness for analytics or testing environments;
- Logging and monitoring – audit logs, detection alerts, response procedures;
- Incident response – whether there is a tested plan, defined roles, and rapid notification protocols;
- Physical security – data‑centre access, device management and secure disposal.
Auditors may sample evidence over the observation period to verify controls are operating consistently. Under SOC 2 guidelines, attestations are annual and cover a defined period.
Step 5: Data‑subject rights and consent procedures testing
Simulate typical requests – access, rectification, deletion, portability and consent withdrawal. Review how requests are logged, how identity is verified, and whether responses meet statutory timelines (normally one month). Evaluate whether automated tools can handle high volumes or unusual requests.
Step 6: Vendor and third‑party processor audit
Review signed DPAs for completeness and verify that vendors meet their contractual obligations, including incident reporting and subprocessor disclosures. Check cross‑border transfer mechanisms (e.g., standard contractual clauses, binding corporate rules). Consider performing on‑site or remote audits of critical vendors.
Step 7: Incident response and breach readiness test
Check whether incident response procedures are documented, regularly tested and aligned with Article 33 of the GDPR. Evaluate the organisation’s ability to detect, investigate and report breaches within 72 hours. Regulators such as HHS describe resolution agreements that last three years and may include significant financial penalties; strong incident response can prevent such sanctions. Test the communication plan (internal and external) and ensure contact details for regulators and affected individuals are accurate.
Step 8: Audit trail and record‑keeping check
Ensure that all significant activities related to data processing (data‑flow changes, consent events, policy updates, breach incidents) are logged with timestamps and version control. Well‑maintained records are critical for demonstrating accountability to auditors and regulatorsdataprotection.ie.
Step 9: Employee interviews and awareness validation
Auditors may interview staff who handle personal data to assess understanding of policies and procedures. This optional step helps validate that training has been effective and that responsibilities are understood at all levels.
Step 10: Reporting and remediation plan
At the conclusion of the audit, the auditor will provide a report detailing findings, risk ratings and recommendations. Internal teams should develop a remediation plan with assigned owners, deadlines and priorities. Track remediation to completion and retain evidence for future audits. Continuous improvement should become part of normal operations rather than a reaction to findings.
Practical Examples and Templates
Being prepared means having structured templates that collect the necessary information in a consistent manner. Here are examples you can adapt to your organisation:
These templates enable busy teams to collect evidence systematically. They can be maintained in spreadsheets, project‑management tools or GRC platforms.
Integrating GDPR Audit Preparation into Ongoing Operations
Preparation should not end when the audit report is delivered. Making audit readiness part of everyday business operations yields long‑term benefits:
- Schedule periodic internal audits – run internal reviews quarterly or biannually to catch drift in controls, update the RoPA and refine policies. Use risk‑based approaches to focus on high‑risk areas.
- Assign ownership – maintain a clear RACI matrix for data protection activities. The DPO (or equivalent) should coordinate with compliance champions in engineering, legal, HR and marketing.
- Embed privacy by design and by default – integrate data‑protection reviews into product development. Conduct DPIAs when new features introduce high‑risk processing. Use data‑minimisation and pseudonymisation techniques during development and testing.
- Provide continuous training and awareness – refresh training content regularly to reflect changes in regulation or technology. Onboard new employees with data‑protection modules and require annual refresher courses.
- Review vendors periodically – maintain a schedule for reviewing vendor DPAs, certifications and breach history. Ensure subprocessors are disclosed and approved. Terminate or renegotiate contracts with vendors who fail to meet security requirements.
Konfirmity’s managed service helps clients maintain these practices by combining automated monitoring with hands-on experts. We operate controls inside your stack and provide continuous evidence, so audit readiness is maintained year‑round rather than in the weeks before an audit.
Challenges and Common Mistakes

- Treating compliance as a one‑time project – organisations that rush to meet a checklist often ignore ongoing maintenance. Without periodic reviews, controls decay and non‑compliance returns.
- Incomplete data inventory – failing to map all data sources and flows leads to blind spots. Hidden data in spreadsheets, logs or third‑party tools can undermine audit results.
- Overlooking third‑party processors – vendors and subprocessors may introduce risks that the controller is responsible for. Without robust DPA reviews and monitoring, a vendor’s breach becomes your liability.
- Weak incident response – many companies lack tested breach notification procedures. Regulators like the U.S. Office for Civil Rights impose multi‑year resolution agreements and hefty fines when incidents are mishandled.
- Insufficient training and unclear accountability – employees who handle personal data may not understand obligations, leading to accidental disclosures. Without clear ownership, tasks fall through the cracks.
- Poor documentation and evidence – missing consent logs, outdated policies and incomplete RoPA entries make it difficult to demonstrate accountability. Evidence must be collected and stored consistently over the observation period.
- Relying solely on vendor assurances – certifications are useful but not sufficient. Verify that vendors implement controls, and request evidence if necessary.
The Payoff: Why GDPR Audit Readiness Is Worth the Investment
Audit readiness is not an academic exercise; it delivers tangible benefits:
- Reduces risk of fines and penalties – by addressing gaps before regulators do, companies avoid the penalties that have totalled billions of euros and millions of dollars. Effective security also reduces breach costs from millions of dollars to significantly less.
- Builds trust with enterprise clients – demonstrating operational security and clear privacy practices accelerates procurement and instils confidence. Enterprise clients increasingly require audit reports and due‑diligence artefacts before signing contracts.
- Streamlines operations – mapping data flows and implementing standard policies simplify integration with new products, regions and partners. Controls built for GDPR often satisfy requirements of other frameworks (ISO 27001, SOC 2, HIPAA), saving time when pursuing multiple certifications.
- Simplifies future audits – continuous evidence collection means that subsequent audits (internal or external) require less effort. Teams avoid last‑minute scrambles and can focus on improvement rather than catching up.
- Supports long‑term resilience – privacy expectations and regulations evolve. A mature data‑protection programme built on accountability and security adapts to new laws, technologies and market demands.
Conclusion
GDPR Audit Preparation is not a checkbox but a strategic, operational discipline. The stakes are high: regulatory fines are steep, and breach costs are rising. Enterprise buyers demand proof that vendors can protect their data. By grounding your programme in the GDPR’s core principles, performing thorough readiness activities, executing the audit with a structured process, and integrating privacy into everyday operations, you not only pass audits but also build lasting trust. Konfirmity’s human‑led, managed service has shown that continuous evidence reduces preparation time by 75% and enables organisations to focus on building products rather than chasing paperwork. Start by assembling your data inventory, reviewing your policies and training your team. The effort you invest now will pay off when enterprise clients ask the hard questions.
Frequently Asked Questions
1. What is the audit process of GDPR?
A GDPR audit assesses how an organisation processes personal data against GDPR requirements. It starts with planning and scoping, followed by data inventory review, policy and documentation audit, technical security review, data‑subject rights testing, vendor assessment, incident response testing, audit‑trail verification and reporting. Evidence must demonstrate lawful bases, transparent notices, security controls and accountability. Continuous improvement after the audit is essential.
2. What are the 7 golden rules of GDPR?
The seven principles of the GDPR are lawfulness, fairness and transparency; purpose limitation; data minimisation; accuracy; storage limitation; integrity and confidentiality; and accountability. These principles guide every data‑processing decision and underpin audit criteria.
3. What is the GDPR right to audit?
Controllers must ensure that processors allow audits and inspections. Data‑processing agreements typically include a right to audit clause permitting the controller or an appointed auditor to verify the processor’s compliance. Regulators may also audit controllers and processors directly, especially after a breach or complaint.
4. How to do audit preparation?
Begin by defining the audit scope and building a comprehensive data inventory (RoPA). Update privacy policies and consent logs to reflect actual practices. Review vendor DPAs, assign a DPO or compliance lead, and train staff. During the audit, provide evidence of lawful bases, security controls, incident response and accountability. After the audit, remediate findings and integrate continuous monitoring so that future audits are smoother and quicker.





.svg)






.svg)
.svg)