ISO 27001 is an international standard that defines how organisations establish, implement, operate and continually improve an information security management system (ISMS). The standard’s power comes from its focus on governance. Annex A control 5.2 requires organisations to define and allocate roles and responsibilities for information security. Having a clear structure ensures that every asset and process is owned by someone and that staff know what they must do. When companies sell to enterprises, this clarity instils confidence that the vendor can handle confidential data and meet contractual obligations.
Clear role allocation is not just about passing an audit. It strengthens the ISMS by clarifying who approves policies, who manages risk, who operates technical controls and who audits the system. It aids compliance because requirements under clauses 4–10 of ISO 27001 depend on assigned accountability. It also builds trust with clients because buyers see that the vendor has people responsible for protecting data. In the following sections we will cover the standard’s structure, the purpose of Annex A 5.2, concepts like accountability and documentation, typical roles and their responsibilities, a step‑by‑step guide to setting up roles, how roles tie into broader ISO 27001 requirements, common pitfalls, why this matters for enterprise sellers and how to maintain your roles matrix over time.
What ISO 27001 Says About Roles & Responsibilities
ISO 27001:2022 consists of high‑level clauses (4 through 10) and a catalogue of detailed controls in Annex A. Clause 5.3 requires top management to assign and communicate responsibilities relevant to the ISMS. Annex A controls supplement the clauses; control 5.2 covers roles and responsibilities.
Purpose of Annex A 5.2
Annex A 5.2’s purpose is to establish a defined, approved and understood structure for implementing, operating and managing information security. The control ensures that each information asset has a designated owner responsible for its protection. Organisations are expected to create a formal structure assigning responsibilities to all employees. The control recognises that smaller organisations may assign multiple responsibilities to a single person, while larger ones might create dedicated teams. Auditors look for evidence that responsibilities are documented and proportionate to the organisation’s size.
Key Concepts: Roles, Responsibilities, Accountability and Documentation
A role refers to a job function or position. Responsibilities define what actions the role must perform and what decisions it can take. Accountability means that a person or function is answerable for the outcome. ISO 27001 expects organisations to avoid vague job descriptions; responsibilities must be clearly documented and communicated. This can be done via employment agreements, internal security policies, procedures or a central responsibility matrix or organisational chart. Documentation should show who is responsible, who approves, who is consulted and who is informed for each control. Smaller organisations may assign multiple roles to one person but must manage conflicts of interest and ensure segregation of duties. Larger organisations often employ dedicated security managers or compliance officers.
Typical Roles and Who Should Own What
ISO 27001 does not prescribe job titles, so companies may adapt the structure to fit their context. The following table summarises common roles and responsibilities relevant for enterprises. (The term ISO 27001 Roles And Responsibilities appears in the first column but is not repeated; the matrix is an example.)
Depending on company size, one person may hold multiple roles. However, separation of duties is essential to reduce conflicts; for instance, the person deploying software should not be the one who approves its deployment.
How to Set Up Roles & Responsibilities (Step‑by‑Step)
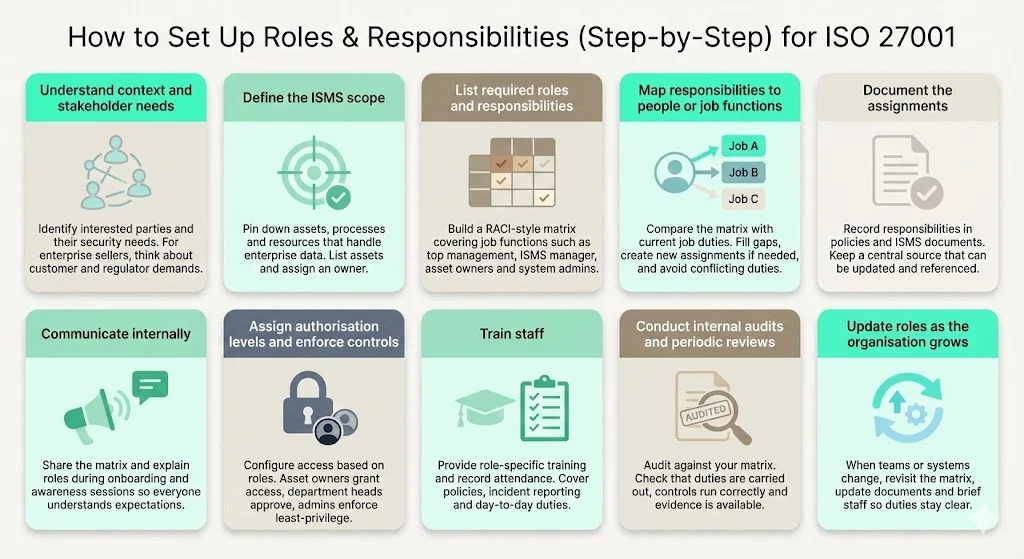
- Understand organisational context and stakeholder needs. ISO 27001 Clause 4.2 requires organisations to identify interested parties (customers, regulators, partners, internal departments) and their security requirements. For enterprise sellers, this includes procurement teams, regulatory authorities and customers with strict security addenda.
- Define the scope of your ISMS. Clause 4.3 mandates defining the ISMS scope. Focus on assets, processes and resources that handle enterprise client data. This will determine which roles are critical. Use an inventory to list assets and assign an owner.
- List required roles and responsibilities. Create a responsibility matrix (e.g., RACI: Responsible, Accountable, Consulted, Informed). This matrix should identify job functions and map them to ISO 27001 Roles And Responsibilities. Include top management, ISMS manager, asset owners, department heads, system administrators, auditors and employees.
- Map responsibilities to people or job functions. Compare your matrix with existing job descriptions. For roles not currently covered, assign responsibilities to specific employees or create new positions. Ensure there is adequate segregation; avoid assigning conflicting duties to the same person.
- Document the assignments. Document responsibilities in employment agreements, internal policies, procedures and the ISMS documentation. Annex A 5.2 emphasises that roles must be documented, communicated and applied consistently across the organisation. Use a central system where the responsibility matrix can be maintained and referenced.
- Communicate internally. Share the matrix and related policies with staff. Present the responsibilities during onboarding and security awareness sessions. This builds an organisational mindset oriented toward security and ensures everyone knows what is expected of them.
- Assign authorisation levels and implement controls. Configure access control based on the assigned roles. For example, asset owners grant permissions to their systems; department heads approve access to departmental resources; system administrators enforce least‑privilege settings. Use identity and access management tools to enforce these decisions.
- Train staff. Provide security awareness training tailored to each role. Training should cover policies, incident reporting procedures and specific responsibilities. Record attendance to demonstrate compliance.
- Conduct internal audits and periodic reviews. Clause 9.2 requires regular internal audits to evaluate the effectiveness of the ISMS and confirm that roles are being followed. Audit teams should verify that responsibilities are executed, controls are operating and evidence is collected. Findings should be reported to management and corrective actions tracked.
- Update roles as the organisation evolves. As you add systems, enter new markets or grow teams, revisit your responsibility matrix. Use management review meetings (Clause 9.3) to reassign duties, update documentation and train staff accordingly. An outdated matrix leads to gaps and overlaps.
By following these steps, companies ensure that ISO 27001 Roles And Responsibilities are not just documented but integrated into operations.
How Roles & Responsibilities Tie Into Broader ISO 27001 Requirements
Defined roles underpin the entire ISMS. They support the confidentiality, integrity and availability triad by clarifying who implements controls, who approves risk treatments and who monitors results. Here are several linkages:
- Governance and leadership. Top management’s commitment is essential. Clause 5.2 requires management to establish an information security policy, allocate resources and ensure communication. Without clear roles, governance falls apart.
- Risk management. Clause 6.1 requires organisations to identify, evaluate and treat risks. Assigning responsibilities ensures someone performs risk assessments, approves treatment plans and verifies that treatments are effective.
- Security policies and documentation. Clause 5.2 emphasises that policies must be approved and communicated. Roles define who writes, reviews and approves each policy and who ensures that documents are current.
- Security controls and authorisation levels. Annex A controls cover asset management, access control, cryptography, operations security, physical security, supplier relationships, incident management, business continuity and compliance. Each control requires an owner. For example, the asset management control (Annex A 5.9) assigns responsibility for maintaining an inventory and classifying assets; access control controls assign responsibility for granting permissions; incident response controls assign roles for detection and reporting.
- Incident response and internal audit. In the event of a breach, clear roles enable a structured response. The IBM report emphasises that quick detection and containment reduce costs. Companies must designate incident managers, technical responders and communicators. Internal audit roles are separate from operations to avoid conflicts, as recommended by the segregation of duties control.
- Compliance enforcement. Clause 10 calls for corrective actions and continual improvement. Assigning responsibilities ensures that corrective actions are owned and tracked. Roles also support compliance with other frameworks (SOC 2, HIPAA, GDPR) because mapping cross‑framework controls requires someone to manage alignment.
Common Challenges & Pitfalls
Implementing ISO 27001 Roles And Responsibilities is not trivial. Companies often encounter issues such as:
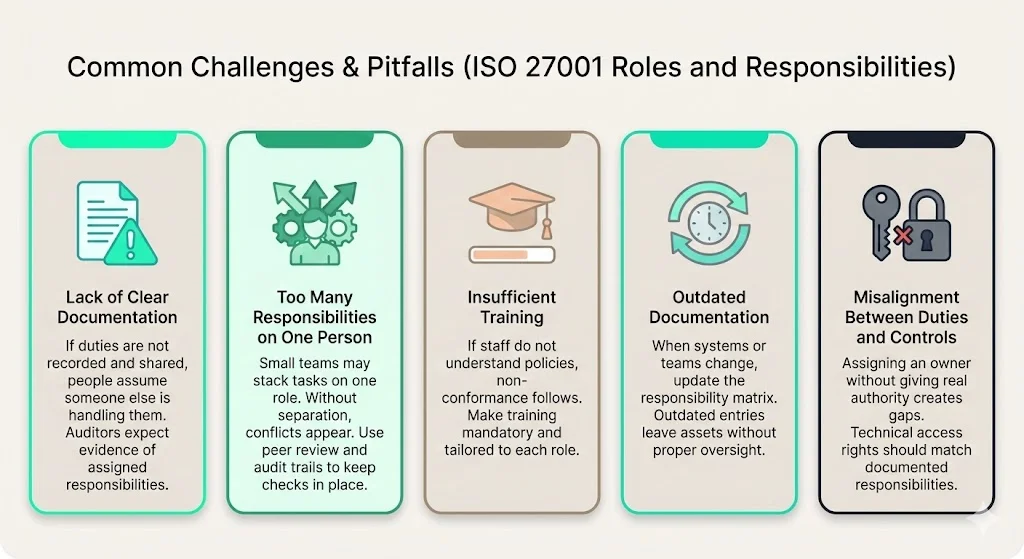
- Lack of clear documentation. If responsibilities are not documented or communicated, staff may assume someone else is responsible, leading to gaps. Auditors look for evidence of assigned responsibilities.
- Too many responsibilities on one person. In small organisations, one person may take multiple roles. Without careful segregation, this can create conflicts (e.g., the person managing the ISMS also auditing it). Use compensating controls such as peer reviews and audit trails.
- Insufficient training. Staff may not understand what the policies require, leading to non‑conformance. Training should be mandatory and role‑specific.
- Outdated documentation. As companies grow or change technology, the responsibility matrix must be updated. Outdated matrices result in unassigned assets and unmonitored controls. Use periodic management reviews to keep documentation current.
- Misalignment between documented responsibilities and technical controls. Assigning an asset owner without ensuring they have the authority to manage permissions defeats the purpose. Access rights must reflect the documented responsibilities.
Why Roles & Responsibilities Matter for Companies Selling to Enterprise Clients
Enterprise clients subject vendors to rigorous due‑diligence. They ask for organisational charts, roles matrices and evidence that security controls are operational. Having ISO 27001 Roles And Responsibilities clearly defined positions your company as trustworthy and reduces sales friction. There are several reasons:
- Proof for audits and vendor assessments. Auditors and customers want documented responsibilities. URM Consulting advises documenting roles in job descriptions, contracts and policies. A matrix shows that there is accountability for each control.
- Reduced risk and faster incident response. The Morgan Lewis analysis of the 2024 cost‑of‑breach report found that breaches lasting more than 200 days cost USD 5.46 million, while breaches contained in less than 200 days cost USD 4.07 million. Clear roles lead to faster detection and containment, saving money.
- Operational efficiency. Konfirmity’s delivery experience across more than 6,000 audits shows that companies that implement structured evidence collection and clear ownership reduce audit preparation time by 75 percent and achieve SOC 2 readiness in 4–5 months compared with 9–12 months for self‑managed programmes. They spend about 75 hours per year on evidence tasks, versus 550–600 hours without a managed service. This efficiency appeals to enterprise buyers who want to see sustained compliance.
- Trust and transparency. Enterprise buyers often share sensitive data such as personal information, financial records or healthcare information. They need assurance that someone owns the systems and processes that protect their data. A responsibility matrix provides that transparency.
- Scalability. As your company grows, an established role structure can be expanded rather than reinvented. New locations or products can inherit the same structure, ensuring consistency.
Sample Structure of a Roles & Responsibilities Matrix
An effective matrix is usually a spreadsheet or table that maps roles to responsibilities, authorisation levels and assets. Here is a simplified example:
You can adapt this structure to your organisation and expand columns to include consulted and informed parties (RACI). The important part is that every control has a person responsible and someone accountable.
Maintenance: Reviewing, Updating and Auditing Roles & Responsibilities
An up‑to‑date responsibility matrix is a living document. To keep it effective:
- Review periodically. Conduct an annual review or whenever there is a significant change in organisation structure, business processes or technology. Review responsibilities as part of the management review meeting.
- Audit adherence. Internal audits should verify that responsibilities are followed. Auditors examine job descriptions, policies and evidence to confirm that staff perform their assigned duties.
- Update documentation. When personnel change roles, update the matrix, policies and access rights. Document changes with version histories to show traceability.
- Communicate changes and retrain. Inform employees of role changes and provide additional training where necessary. For example, when a department head becomes the asset owner for a new system, ensure they know how to manage access and classify data.
- Log changes and decisions. Keep a change log. This helps auditors see that the organisation manages its ISMS proactively and supports continual improvement.
Conclusion
Implementing ISO 27001 Roles And Responsibilities is foundational for strong security, effective risk management and credibility with enterprise clients. By clearly defining who owns what, documenting responsibilities, providing training and periodically auditing compliance, organisations transform the standard from a document into an operational practice. In a market where data breach costs exceed USD 4 million and regulated buyers demand evidence, mere policies are not enough. Companies that start with security and treat compliance as an outcome save time, reduce risk and close deals faster. A human‑led managed service like Konfirmity’s ensures that responsibilities are implemented inside your stack, monitored continuously and ready for audits year‑round—turning security into a trusted business enabler.
FAQs
1) What is the role and responsibilities matrix in ISO 27001?
A role and responsibilities matrix is a table or spreadsheet that maps job functions to specific information security duties and levels of authority. It clarifies who is responsible (does the work), who is accountable (owns the outcome), who is consulted and who is informed for each control. Annex A 5.2 requires roles and responsibilities to be defined and allocated according to the organisation’s needs.
2) What are the responsibilities of ISO 27001 management?
Top management must commit to and approve the ISMS, define the security policy, provide resources, set objectives, support risk management and ensure communication across the organisation. They must also review ISMS performance and direct corrective actions.
3) What is the ISO clause for roles and responsibilities?
Annex A 5.2, titled Information Security Roles and Responsibilities, requires organisations to define and allocate information security roles. Clause 5.3 in the main body of ISO 27001 also requires management to assign and communicate responsibilities and authorities.
4) What are the six central security areas under ISO 27001?
While ISO 27001 includes many controls, six broad areas relevant to roles and responsibilities are: (1) organisational governance and leadership (policies, management commitment); (2) asset management (inventory, classification and ownership); (3) access and identity management (authentication, authorisation and reviews); (4) human resource security (training, screening, termination procedures); (5) technical controls (system configuration, encryption, network security, vulnerability management); and (6) incident response and compliance (detection, reporting, internal audit, corrective actions). Having defined roles ensures that each area is managed effectively.





.svg)






.svg)
.svg)